“Hacking” as cracking and illegal compromise of accounts and systems online is now called, is a big industry. A hacked WordPress site (many of them are) can easily bring in $1 to $20 a day for the operator. This does not sound like much but if you control thousands of these hacked sites and live out of reach of countries prone to prosecute you it can be a really good income.
So that is why we have companies that protect things like websites, email and social media accounts. Local Law Enforcement still has to be given a finger puppet show to explain what the complaint is, what law was broken and why they should care (its been getting better over the years, but still quite slow) so we need security companies and security services to act where Law Enforcement cannot or refuses to act. They also serve as intermediaries between Law Enforcement, Web hosting companies and web sites and can make a frustrating situation easier…for a price.
The other day I had a wave of curiosity about this. I wondered if anyone who offered a security service for “hacking” would also offer a hacking service.
It would be a good plan. You could use your leads created by the hacker for hire site to solicit customers for your white hat website.
So I googled “hackers for hire” and eventually found an article written by Matthew Goldstein found here:
Need Some Espionage Done? Hackers Are For Hire Online
The article is about a website called Hackers List. This is a clearing house for services that are often illegal and the site owners get a cut once a job has been finished. (from the article)
“It is done anonymously, with the website’s operator collecting a fee on each completed assignment. The site offers to hold a customer’s payment in escrow until the task is completed.”
Some of the things quoted on Hackers List are this:
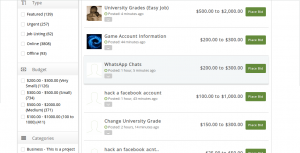
University Grade alteration (hacking into School computers was illegal last time I looked…I never looked…I have guessed this and I assume I am correct) facebook accounts and an odd thing called McKinnley for $200 to $300 (I was tempted to join as “Czolgosz” and bid on that one) so seems like the site owners are making money off of crime and benefiting from both volume of business and price.
The really interesting part came later in the article when an ethical hacking company or White Hat was quoted:
“Still, the market for hackers, many of whom comply with the law and act more like online investigators, shows no signs of slowing. Many companies are hiring so-called ethical hackers to look for weaknesses in their networks.
David Larwson, a director of operations with NeighborhoodHacker.com, which is incorporated in Colorado, said he had seen increased demand from companies looking to make sure their employees are not obtaining sensitive information through hacking. He said in an email that companies were increasingly focused on an “insider threat” leading to a breach or unauthorized release of information.
On its website, NeighborhoodHacker describes itself as a company of “certified ethical hackers” that works with customers to “secure your data, passwords and children’s safety.” “
I did some checking and found out that the two companies, neighborhoodhacker.com and hackerslist.com seem to have the connection making both a Grey Hat company (one being a conduit for legal security work and the other being a conduit for illegal work and profiting from both)
The WHOIS of NEIGHBORHOODHACKER.COM
Domain Name: NEIGHBORHOODHACKER.COM
Registry Domain ID:
Registrar WHOIS Server: whois.1api.net
Registrar URL: http://www.1api.net
Updated Date: 2014-03-30T21:48:40Z
Creation Date: 2012-05-04T22:20:32Z
Registrar Registration Expiration Date: 2016-05-04T22:20:32Z
Registrar: 1api GmbH
Registrar IANA ID: 1387
Registrar Abuse Contact Email: abuse@1api.net
Registrar Abuse Contact Phone: +49.68416984×200
Reseller: iwantmyname http://iwantmyname.com
Domain Status: ok
Registry Registrant ID:
Registrant Name: Neighborhood Hacker
Registrant Organization: Neighborhood Hacker LLC
Registrant Street: 590 w hwy 105 ste 274
Registrant City: Monument
Registrant State/Province: CO
Registrant Postal Code: 80132
Registrant Country: US
Registrant Phone: +1.8889660937
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: charles@charlestendell.com
Registry Admin ID:
Admin Name: Neighborhood Hacker
Admin Organization: Neighborhood Hacker LLC
Admin Street: 590 w hwy 105 ste 274
Admin City: Monument
Admin State/Province: CO
Admin Postal Code: 80132
Admin Country: US
Admin Phone: +1.8889660937
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: info@neighborhoodhacker.com
Registry Tech ID:
Tech Name: Neighborhood Hacker
Tech Organization: Neighborhood Hacker LLC
Tech Street: 590 w hwy 105 SOE 274
Tech City: Monument
Tech State/Province: CO
Tech Postal Code: 80132
Tech Country: US
Tech Phone: +1.8889660937
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: info@neighborhoodhacker.com
Name Server: ns01.domaincontrol.com
Name Server: ns02.domaincontrol.com
DNSSEC:
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net/
And the WHOIS of HACKERSLIST.COM before the 1/15/2015 article
Registry Domain ID: 1882636295_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.1api.net
Registrar URL: http://www.1api.net
Updated Date: 2014-10-28T19:43:27Z
Creation Date: 2014-10-28T19:43:25Z
Registrar Registration Expiration Date: 2015-10-28T19:43:25Z
Registrar: 1API GmbH
Registrar IANA ID: 1387
Registrar Abuse Contact Email: abuse@1api.net
Registrar Abuse Contact Phone: +49.68416984×200
Reseller: iwantmyname http://iwantmyname.com
Domain Status: clientTransferProhibited – http://www.icann.org/epp#clientTransferProhibited
Registry Registrant ID:
Registrant Name: Charles Tendell
Registrant Organization:
Registrant Street: 590 W Hwy 105 ste 274
Registrant City: Monument
Registrant State/Province: CO
Registrant Postal Code: 80132
Registrant Country: US
Registrant Phone: +1.7204320389
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: info@neighborhoodhacker.com
Registry Admin ID:
Admin Name: Charles Tendell
Admin Organization:
Admin Street: 590 W Hwy 105 ste 274
Admin City: Monument
Admin State/Province: CO
Admin Postal Code: 80132
Admin Country: US
Admin Phone: +1.7204320389
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: info@neighborhoodhacker.com
Registry Tech ID:
Tech Name: Charles Tendell
Tech Organization:
Tech Street: 590 W Hwy 105 ste 274
Tech City: Monument
Tech State/Province: CO
Tech Postal Code: 80132
Tech Country: US
Tech Phone: +1.7204320389
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: info@neighborhoodhacker.com
Name Server: ns1.iwantmyname.net 62.116.159.99 2001:4178:0003:a357:0062:0116:0159:0099
Name Server: ns3.iwantmyname.net 89.146.248.96 2a01:0130:2000:0118:0089:0146:0248:0096
Name Server: ns4.iwantmyname.net 74.208.254.95
Name Server: ns2.iwantmyname.net 217.160.113.131 83.169.55.71 2a01:0488:2000:0c02:0083:0169:0055:0071
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net/
And on January 16th 2015, one day after the article appeared.
Domain Name: HACKERSLIST.COM
Registry Domain ID: 1882636295_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.1api.net
Registrar URL: http://www.1api.net
Updated Date: 2014-10-30T10:21:01Z
Creation Date: 2014-10-28T19:43:25Z
Registrar Registration Expiration Date: 2015-10-28T19:43:25Z
Registrar: 1API GmbH
Registrar IANA ID: 1387
Registrar Abuse Contact Email: abuse@1api.net
Registrar Abuse Contact Phone: +49.68416984×200
Reseller: iwantmyname http://iwantmyname.com
Domain Status: clientTransferProhibited – http://www.icann.org/epp#clientTransferProhibited
Registry Registrant ID:
Registrant Name: David Harper
Registrant Organization:
Registrant Street: Po Box 11671
Registrant City: Wellington
Registrant State/Province: CO
Registrant Postal Code: 6142
Registrant Country: NZ
Registrant Phone: +64.11111111
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: 1534387e@opayq.com
Registry Admin ID:
Admin Name: David Harper
Admin Organization:
Admin Street: Po Box 11671
Admin City: Wellington
Admin State/Province: CO
Admin Postal Code: 6142
Admin Country: NZ
Admin Phone: +64.11111111
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: 1534387e@opayq.com
Registry Tech ID:
Tech Name: David Harper
Tech Organization:
Tech Street: Po Box 11671
Tech City: Wellington
Tech State/Province: CO
Tech Postal Code: 6142
Tech Country: NZ
Tech Phone: +64.11111111
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: 1534387e@opayq.com
Name Server: duke.ns.cloudflare.com
Name Server: gene.ns.cloudflare.com
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net/
We can see some similarities here that are hard to deny.
I contacted tech support for a quote from both companies and both support technicians were not able to comment either due to lack of knowledge or company policy (both were very polite).
I do not think it is unreasonable to question the practices of both companies. Or to one Charles Tendell who, according to his web site, is a Certified Ethical Hacker.
http://charlestendell.com/
http://charlestendell.com/about/certifications/
http://azoriancybersecurity.com/
Also for Fox News and Lockheed Martin. I do not know, perhaps it is a smear job against Mr. Tendell (always possible) but I would think most smear jobs would be better known and not found out because some guy with a day off had a brain fart and access to google and whois.
—update—
Not a smear job. New York Times article will be up on 5/13/2015

